Summary
As the significance of outgoing email threats continues to grow, compliance with security requirements has become imperative. The need to implement robust security measures has become crucial in safeguarding against these evolving threats. In the forthcoming discussion, we will delve into the specific email security requirements, focusing on the diverse threats and vulnerabilities associated with outgoing emails. This comprehensive exploration addresses the security requirements necessary for responding to both intentional and unintentional information leakage, account extortion attacks, and unauthorized email server access. It outlines specific requirements, including restrictions on email sending conditions, the prevention of unauthorized server access, and the incorporation of advanced threat detection technology. These prescribed actions are critical to mitigating the risks linked to intentional information disclosure and preventing unauthorized access to email servers.
Security Requirements for Countering Outbound Email Threats by Users
● Security Requirements for Countering Intentional Information Leakage
To counter outgoing email threats related to international information leakage, security managers should be empowered with the authority to set specific email sending conditions. Strengthening the prevention of intentional information leakage requires establishing conditions that meet security policies. Moreover, if the predefined sending conditions are not met, a key recommendation is to grant managers the authority to reassess and potentially withhold email transmissions. This proactive approach ensures a real-time evaluation and intervention mechanism against intentional data breaches. By entrusting managers with the control over email sending conditions, organizations can strengthen their defenses and effectively mitigate risks associated with intentional information disclosure.
● Security Requirements for Countering Unintentional Information Leakage
Systems should provide warnings or automatically block users from replying to or sending emails to email addresses identified as malicious. Moreover, secure email conversion is essential for safely transmitting large attachments from an isolated internal network to an external one. To prevent data leakage, senders should have the capability to recall sent emails. Additionally, it is advisable to encrypt the contents of outgoing emails meeting specific conditions, such as the IP address that confirmed the email and the number of times the email was opened.
Security Requirements for Countering Outbound Email Threats by Attackers
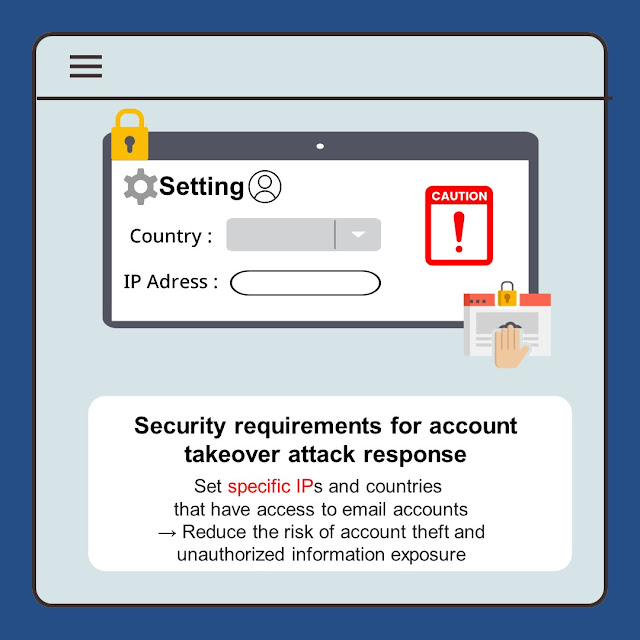
● Security Requirements for Countering Attacks Using Account Take-over
It is crucial to establish strict security requirements to address outgoing email threats, including attacks and account theft through malicious codes. In scenarios where a user's account is compromised via an email attack using malware, sensitive information can be sent and leaked. Security requirements for countering this attack should enable users to configure specific IPs and countries allowed to access their email accounts, granting them control against unauthorized access and potential data leakage.
Implementing IP and country-based restrictions on email account access is a key strategy to mitigate the risk of account theft and unauthorized information exposure. By specifying the IP addresses and countries from which email accounts can be accessed, organizations significantly reduce the likelihood of security breaches. Additionally, when sending emails, countering the threat of zero-day malware attacks involves action-based analysis checks. These checks aim to detect new viruses that are not registered in existing patterns. Alerts for newly discovered or detected malicious codes should be promptly reported through manual or automated processes. Regular monitoring and analysis enhance the overall cybersecurity posture, providing robust defense against outgoing email threats. Ongoing user training on recognizing and reporting suspicious activities further strengthens the organization’s resilience against potential security breaches.
● Security Requirements for Countering Unauthorized Email Server Access Attacks
Establishing robust security requirements is essential for effectively responding to unauthorized email server access attacks. Firstly, implementing access controls to restrict access from specific countries is a critical preventive measure against unregistered email server access attacks. Secondly, in the event of an unauthorized email server attack, it is crucial to precisely identify detailed access information and ensure that access requests triggered by such attacks are not forwarded to the email server. Finally, blocking unregistered Simple Mail Transfer Protocol (SMTP) and country access is imperative. Notably, blocking email transmissions when the sender's SMTP information does not match the recipient's SMTP information is a key security measure. This prevents malicious actors from exploiting the information mismatches. Integrating these comprehensive security measures empowers organizations to effectively enhance their defenses and mitigate the risks associated with unauthorized email server access attacks.
In wrapping up, this article underscores the critical need for robust security requirements in the realm of email security, highlighting the imperative for organizations to remain proactive and adaptable in the face of evolving cyber threats. The key takeaways advocate for the adoption of robust email security practices, the implementation of data protection policies grounded in industry best practices, and the embrace of technology solutions rooted in international standards, including encryption and advanced threat detection. Organizations can secure their outbound email communications by complying with international standards and incorporating continuous monitoring and analysis, thereby establishing a secure and resilient cyber environment. Regular adherence to standards and the integration of tools like Mail Inspector become pivotal in securing against outbound email threats. This proactive strategy not only aids in identifying and resolving potential issues related to outbound emails but also serves as a preventative measure against inadvertent information disclosure. In essence, a comprehensive defense strategy that combines technical security solutions with ongoing monitoring forms a vital framework to effectively address and mitigate outbound email threats, ensuring a steadfast and secure cyber landscape.
References
<Outbound Email Security>
Outbound Email Security (powerdmarc.com)
<What is Outbound Email Protection?>
https://ironscales.com/glossary/outbound-email-protection
<Data Leakage - the risk, the reality and messaging channels>
:https://www.leapxpert.com/data-leakage-the-risk-the-reality-and-messaging-channels/
<Security requirements and countermeasures for targeted email attacks>
https://www.itu.int/ITU-T/recommendations/rec.aspx?rec=15710&lang=en






![[Media] XSS Attacks Across SNS: A Historical Analysis](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg1PB2eQDHDkUQntp2VK8pqovijupQN4tsrV42fIq9vBw8TYis-BnTLjbZb2hLTnDMTM5PtTdnZTwHCaBsRCLPdYMEkmi3UboL_qpWnczwCT6E66xtBzYodLKKDaWPTOJRh5BYjfp5murVjPZ18Oz_6fjJK7mRrvalwrWijFM5vkRbDQza_ISTQlm3kM4Y/w72-h72-p-k-no-nu/%EC%8D%B8%EB%84%A4%EC%9D%BC.png)


![[Zero-day] Understanding zero-day attacks](https://blogger.googleusercontent.com/img/a/AVvXsEh2lWUhaQgbBMUsEIaEMq4-_EG0s_bz-VKacjDbO8N4TrTF1saQogoT6V2gDz7U8qaEJA-SMj3ngkstaZXyhjhGOrVIo8dJbrCnZptivX0XefGYiwoIr36kcsPMY6IQ_1J_3FyOOa0BKyVwXVOT48_5tUaK9RJRWxFiIgUM6mLm7YMA8EXUg3r3SA9I26U=w72-h72-p-k-no-nu)



0 Comments