Introduction
Email spoofing has emerged as a dangerous element in cyber attacks, particularly against corporations. This deceptive technique involves fraudulent links, impersonation, and evolving threat methods, making it a formidable challenge for defense. Cloudflare, a web service and security company, conducted an analysis of 250 million malicious emails sent over a year starting May 2022. Their findings revealed that over 35.6% of these emails, more than a third of detected threats, contained fraudulent links. Clicking on such links exposes users to landing pages controlled by attackers, resulting in credential theft, remote code execution, network damage, and other harms. A notable tactic within email spoofing is “domain spoofing”, where cybercriminals create similar malicious domains that closely resemble those of legitimate organizations. This enables them to create email addresses that appear nearly legitimate.
Last year, domain spoofing for identity impersonation experienced significant growth, rising from 3.9% to 14.2% among detected threats. Microsoft was the most impersonated company, accounting for 9.9% of cases, closely followed by Boeing at 9.7%. The top 10 most frequently impersonated companies included the World Health Organization (WHO), Google, SpaceX, Salesforce, Apple, Amazon, and T-Mobile. Cloudflare's research highlights that brand impersonation targets highly popular companies, with 60% of email phishing incidents involving the impersonation of globally renowned brands. Similar domains are used to mimic legitimate entities, conducting to various cyber attacks, including email spoofing.
1. Understanding Spoofing in Cybersecurity
The term “spoofing” in the realm of IT refers to techniques designed to deceive victims by presenting false information or connections, all without directly infiltrating systems. It differs from phishing, which exploits vulnerabilities, and sniffing, which involves intercepting information. Spoofing actively lures users into trusting and accepting inaccurate information.
In spoofing attacks, users are led to believe and access malicious sites or provide sensitive information to attackers based on false information or connections introduced by the attacker. What adds to the danger is the potential for more significant secondary damages, especially when combined with phishing. While phishing typically involves planting malware and waiting for a user to be deceived into connecting, presenting phishing methods directly to users without easy detection makes it an especially nefarious attack strategy.
2. Principles and Types of Spoofing Attacks
Spoofing attacks are based on the exploitation of trust, where attackers mimic legitimate sources, using the inherent trust that users or systems place in familiar entities. This can involve imitating email addresses, websites, network addresses, or even biometric data. The primary goals of spoofing attackers typically include stealing critical data, spreading malicious software, or bypassing access control.
The damages resulting from spoofing attacks are diverse, ranging from unauthorized access to critical information through data theft, delivery of harmful software to victim systems, and fraud via identity theft, to unauthorized access leading to network damage, direct financial theft, or indirect costs incurred through embezzlement responses. Spoofing can manifest in various forms, such as DNS spoofing, ARP spoofing, or IP spoofing, and may occur in combination.
Email spoofing is a prevalent tactic, constituting 90% of cyber attacks. Common email spoofing techniques involve attacks with similar email address attacks, often leading to cascading URL phishing attacks. The main objective of email spoofing is to deceive recipients into believing that the email is from a trusted sender for malicious purposes. Attackers manipulate the sender address in the email header to appear as if it is sent from a reputable company, government agency, or a known colleague - a source the recipient trusts. This manipulation can result in phishing URL attacks, where users are tricked into clicking on malicious URLs and entering login credentials or other critical information. Therefore, effective solutions for identifying similar email addresses and countering attacks involving phishing URLs are crucial to prevent email spoofing.
3. Methods and Solutions to Prevent Spoofing
Detecting spoofing, designed to deceive users, is inherently challenging. To avoid the risks of falling victim to spoofing attacks, several methods can be employed, incorporating strong authentication protocols, data encryption, regular software updates, and proactive network monitoring.
Communication Protocol Authentication:
Implement authentication protocols such as Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC). These protocols verify the sender's compliance, aiding in the detection of forged sender addresses. By ensuring adherence to these protocols, the authenticity of the sender can be verified, preventing the delivery of spoofed emails or messages.
Data Encryption:
Employ encryption techniques to safeguard the content of emails and attachments, ensuring that only the intended recipient can access the information. Considerations include establishing conversion conditions, reviewing the security risk of attached files, encrypting external network path information within attachments, and reviewing URL information.
Effectively preventing complex spoofing attacks in emails requires adherence to security requirements concerning both similar email addresses and phishing URLs. Complying with established standards is essential to bolster email security against sophisticated spoofing attempts.
 |
In combating spoofing using similar email addresses, the standard [8.2.2 Security requirements for countering look-alike domain attacks] outlines the following security requirements: Users should be notified of the risk similarity level when the sender's domain is detected as a look-alike domain based on accumulated email history, and such emails should be blocked.
The difference in the number of characters in the email address should be used as a criterion for determining fraudulent look-alike email attacks.
Top-level domains (TLDs) that are different should be managed separately.
It is advisable for security managers to manually register suspicious email addresses that appear fraudulent.
In line with these security requirements, the standard [9.2.2 Countermeasures for look-alike domain attacks] suggests the following solutions:
Implement a domain similarity calculation method that involves accumulating sender domains of inbound emails. Newly received emails can be compared and analyzed against these accumulated domains. Inbound emails are temporarily suspended or blocked when the top-level domain (TLD) is modified, the order of the string array changes, or one of the strings is replaced with a similar character. It is not recommended to determine domain similarity based only on the difference in the number of characters.
Domain similarity calculations accumulate the sender domains of inbound emails and then analyze newly received emails against the accumulated domains. Inbound emails are suspended or blocked when a top-level domain (TLD) is modified, an array of strings is reordered, or a set of strings is created by changing one of the strings to a similar character or characters. It is not recommended to determine domain similarity based on simple differences in the number of characters.
The security requirements for similar email addresses against phishing URLs according to the ITU-T X.1236 [8.2.4 Security requirements for countering URL phishing attacks] are as follows:
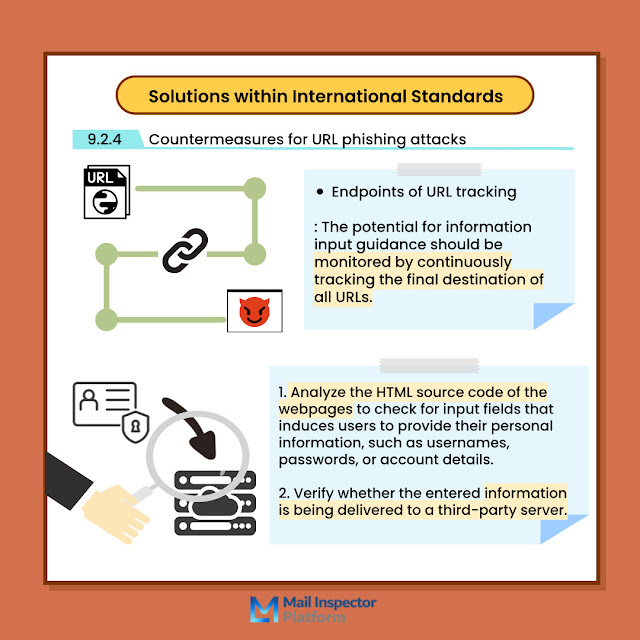
The final destination of URLs, particularly those containing web pages designed to induce the entry of personal information, must be continuously tracked.
In accordance with these security requirements, the standard [9.2.4 Countermeasures for URL phishing attacks] suggests the following solutions:
Endpoint of URL Tracking: All URLs should be tracked to their final destination to monitor the likelihood of guidance for information entry.
Analyze the HTML source code of web pages to check for input boxes that induce users to provide personal, ID, or password information, and inspect whether the entered information is transmitted to a third-party server.
Spoofing, a prevalent technique in cyber attacks, capitalizes on deceiving victims into trusting false information or connections without direct system infiltration. This method is extensively employed in emails, which constitute a substantial 90% of cyber attacks. To prevent financial losses and data leaks due to spoofing, users must acquire the ability to recognize suspicious emails. Additionally, adhering to security policies designed to counter complex spoofing attacks is paramount.
The international email security standard, officially recognized by the International Telecommunication Union (ITU), a specialized UN agency, offers comprehensive security requirements and solutions for combating spoofing. Embracing a proactive stance against diverse cyber threats necessitates a deep understanding of attack types and a commitment to proactive measures aligned with security requirements.
Continuously aligning cybersecurity practices with the international standard provides a robust defense not only against spoofing but also against evolving hacking techniques. By staying informed about the standard and consistently assessing cybersecurity in its light, organizations can proactively fortify their resilience against cyber threats.
References
<Security requirements and countermeasures for targeted email attacks>
https://www.itu.int/ITU-T/recommendations/rec.aspx?rec=15710&lang=en
<Key Takeaways from the 2023 Domain Impersonation Report>
https://www.tripwire.com/state-of-security/key-takeaways-2023-domain-impersonation-report
<SMTP Smuggling - Spoofing E-Mails Worldwide>
https://sec-consult.com/blog/detail/smtp-smuggling-spoofing-e-mails-worldwide/














![[Media] XSS Attacks Across SNS: A Historical Analysis](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg1PB2eQDHDkUQntp2VK8pqovijupQN4tsrV42fIq9vBw8TYis-BnTLjbZb2hLTnDMTM5PtTdnZTwHCaBsRCLPdYMEkmi3UboL_qpWnczwCT6E66xtBzYodLKKDaWPTOJRh5BYjfp5murVjPZ18Oz_6fjJK7mRrvalwrWijFM5vkRbDQza_ISTQlm3kM4Y/w72-h72-p-k-no-nu/%EC%8D%B8%EB%84%A4%EC%9D%BC.png)


0 Comments